How it works
Secret headers work by:- Client-side invisibility: Headers configured as secret are not visible to the client browser
- Server-side forwarding: Edgee automatically forwards these headers to your backend server
- Secure transmission: Headers are transmitted securely through Edgee’s infrastructure
- Backend validation: Your server can validate these headers to ensure requests come from Edgee
Configuration
To enable secret headers, navigate to your project’s Security settings and click on the Secret Headers section.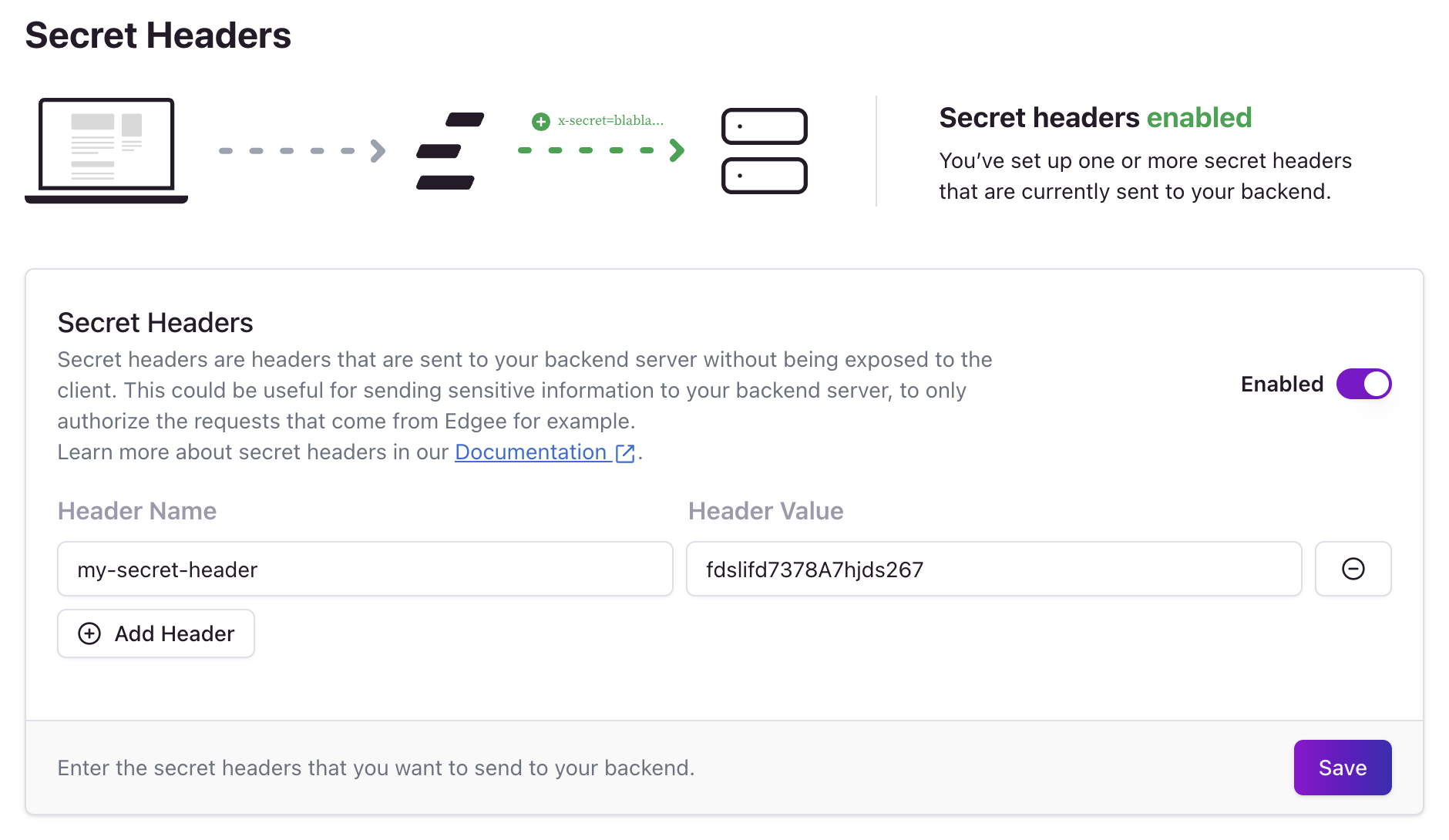
Go to your project > Security > Secret Headers to configure secret headers.
Enabling Secret Headers
- Toggle the switch: Click the toggle switch to enable or disable secret headers
- Add headers: Click the Add Header button to add new secret headers
- Configure headers: For each header, specify:
- Header Name: The name of the HTTP header (e.g.,
X-Edgee-Token) - Header Value: The value of the header (e.g., your secret token)
- Header Name: The name of the HTTP header (e.g.,
- Save configuration: Click Save to apply your changes
Header Management
- Add headers: Use the Add Header button to add multiple secret headers
- Remove headers: Click the minus icon next to any header to remove it
- Edit headers: Modify header names and values at any time
- Validation: The system validates header names and values before saving
Use Cases
Example: API Authentication
Use secret headers to authenticate API requests from Edgee:Backend Implementation
Node.js Example
Python Example
Go Example
Security Best Practices
- Use strong values: Choose complex, random values for your secret headers
- Rotate regularly: Periodically update your secret header values
- Validate on backend: Always validate secret headers on your backend server
- Monitor usage: Track and monitor requests using secret headers
- Limit scope: Only use secret headers for necessary authentication/authorization

