Skip to main contentEdgee’s rate limiting feature protects your website or application from abuse at the edge, before requests reach your origin server.
This helps prevent DDoS attacks, brute force attempts, and other forms of abuse while ensuring legitimate traffic continues to flow.
How it works
Rate limiting works by:
- Evaluating rules in order: Rules are evaluated by their rank (lowest rank first)
- Creating unique client keys: Each request is identified by a unique key based on configurable criteria
- Tracking request rates: Requests are counted within configurable time windows
- Applying limits: When a client exceeds the rate limit, they are blocked for a specified duration
- Returning 429 responses: Blocked clients receive a “Too Many Requests” response
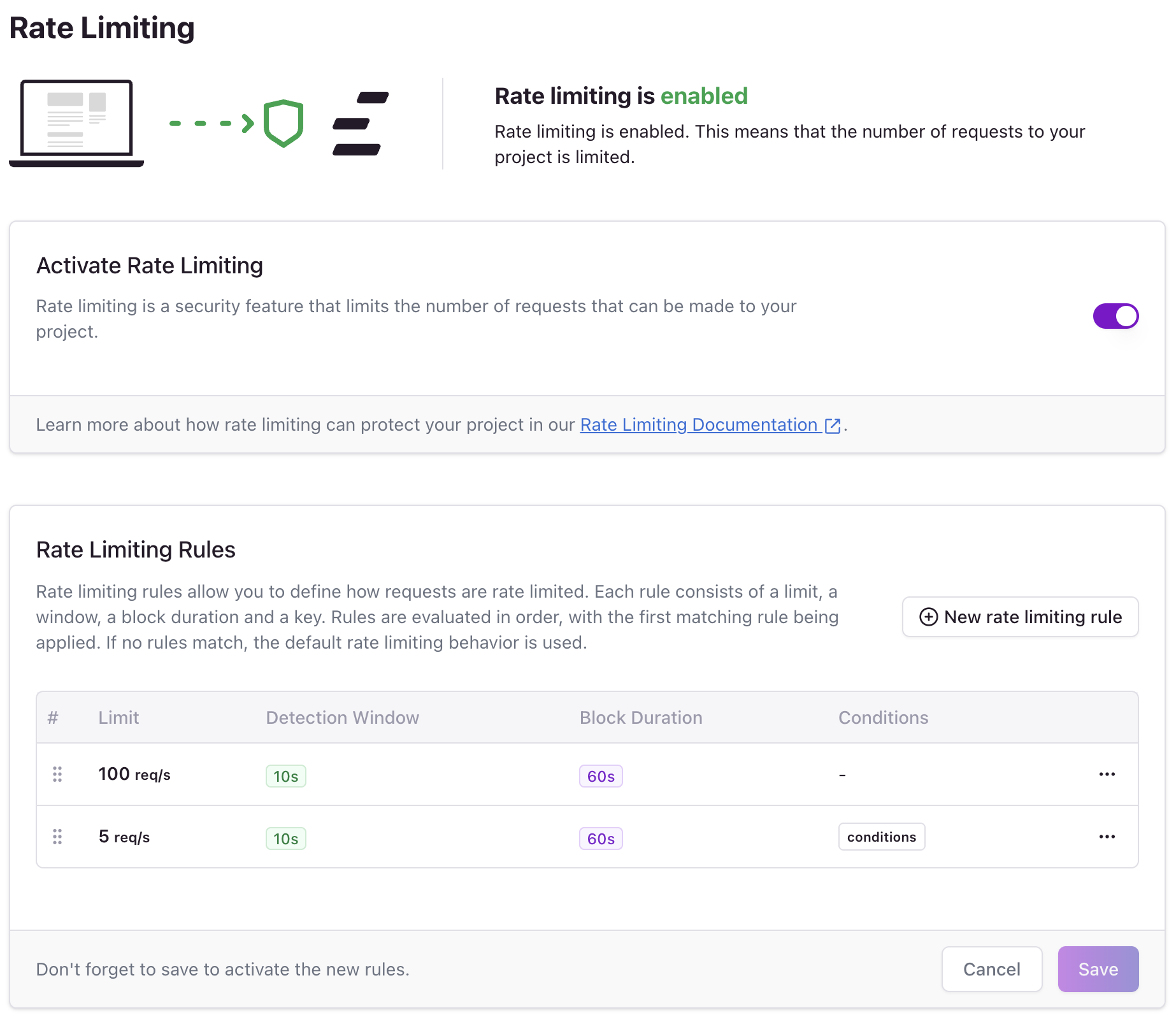
Configuration
To enable rate limiting, click on the Activate rate limiting switch.
Rate limiting is configured through on or more rules. Each rule defines specific rate limiting behavior.
Basic Rule Configuration
Click on the New rate limiting rule button to add a new rule, then fill the form with the following properties:
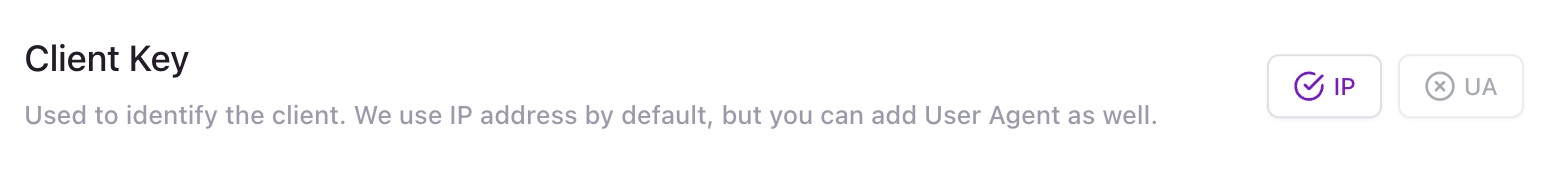
Client Key
The client key determines how requests are grouped for rate limiting.
By default, the client key is the client’s IP address. You can also use the User-Agent header to the key, or both.
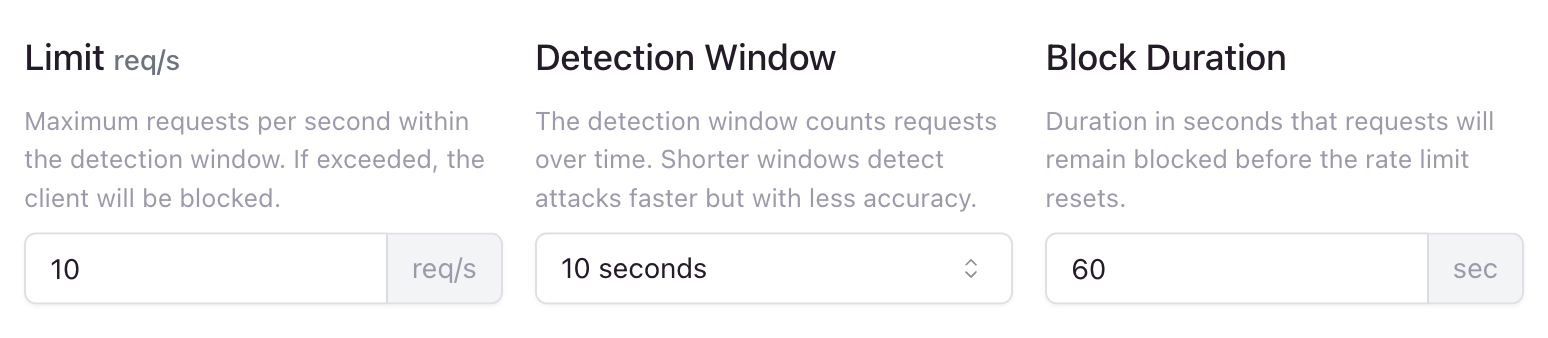
Rate Limit Fields
- Limit: The maximum number of requests per second within the rate window.
- Window: The time window for counting requests. You can choose between
1 second, 10 seconds or 60 seconds.
- Block Duration: The duration to block clients when rate limit is exceeded.
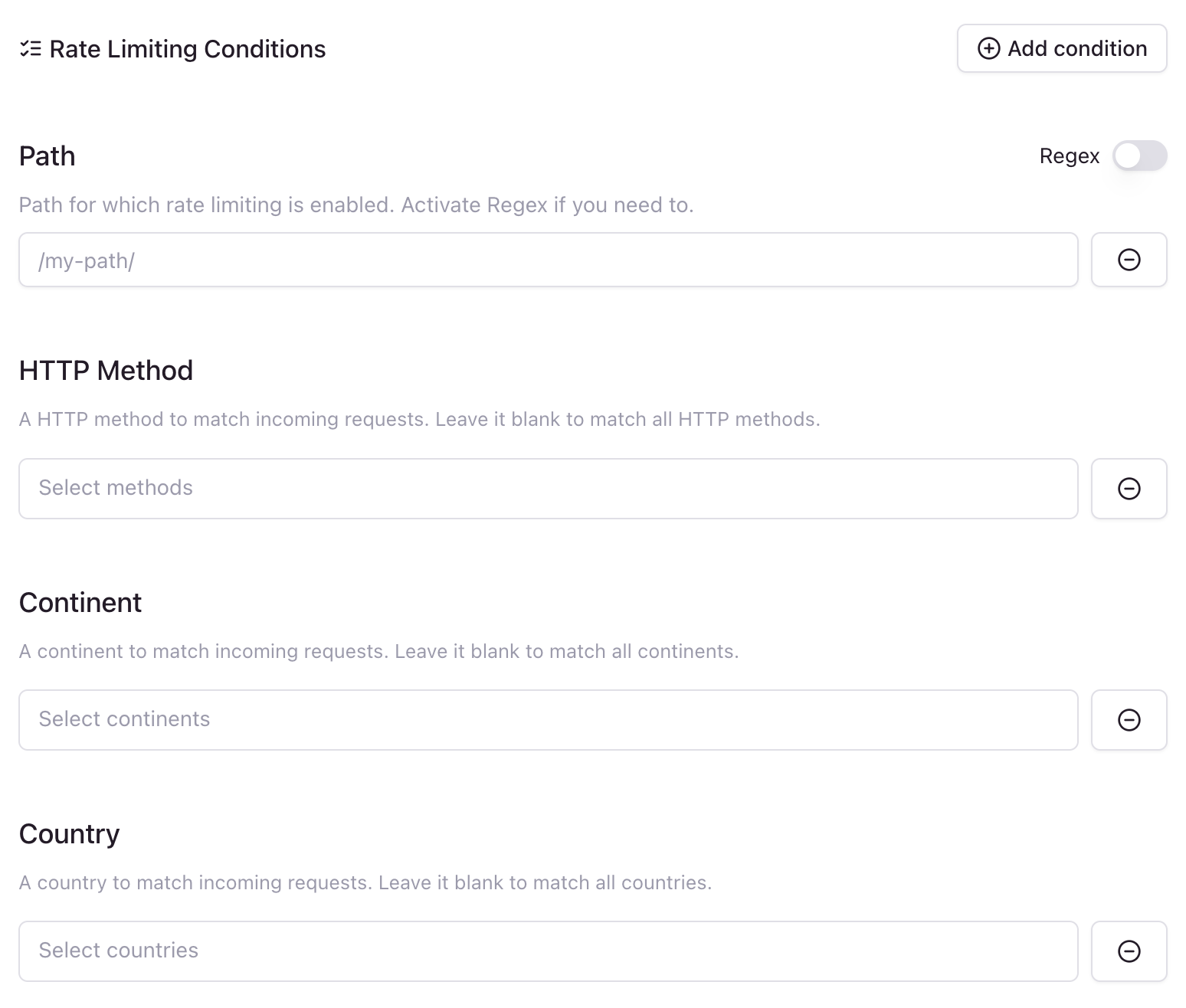
Advanced Configuration with Conditions
To optionally add conditions to the rule, click on the Add condition button, so rate limiting will be applied only to requests that match the conditions.
For example, you can apply the rate limiting only to requests to a specific path, or only to requests from a specific country.
- Path: The path to apply the rate limiting to. You can use a regular expression to match the path.
- Method: The HTTP method to apply the rate limiting to. You can choose between
GET, POST, PUT, DELETE, HEAD, OPTIONS, PATCH or CONNECT.
- Continent: The continent to apply the rate limiting to.
- Country: The country to apply the rate limiting to.
Example 1: API Protection
Protect your API endpoints with stricter limits:
- For API protection, set up a rule with:
- 5 requests per 10 second window
- 2 minute block duration when exceeded
- Use IP for client identification
- Apply only to paths starting with
/api/ using regex matching
Example 2: Geographic Rate Limiting
Apply different limits based on geographic location:
For geographic-based rate limiting, set up two rules:
Rule 1 - Strict limits for specific countries:
- Set rank to 1 (higher priority)
- Set limit to 1 request per 10 seconds
- Set block duration to 5 minutes
- Add condition for specific countries
Rule 2 - Higher limits for trusted regions:
- Set rank to 2 (lower priority)
- Set limit to 100 requests per 10 seconds
- Set block duration to 1 minute
- Add condition for Continent and select Europe and North America
Example 3: Method-Specific Limits
Apply different limits based on HTTP method:
Rule 1 - Strict limits for write operations:
- Set rank to 1 (higher priority)
- Set limit to 2 requests per 10 seconds
- Set block duration to 3 minutes
- Add condition for Method and select POST, PUT, DELETE
Rule 2 - Higher limits for read operations:
- Set rank to 2 (lower priority)
- Set limit to 50 requests per 10 seconds
- Set block duration to 1 minute
- Add condition for Method and select GET
Response Codes
When a client exceeds the rate limit, Edgee returns:
- HTTP Status:
429 Too Many Requests
- Response: A custom 429 error page
- Headers: Standard rate limiting headers